Scam jobs: Fake tales target gullible netizens
Manama : Scam job websites may promise lots of work, but all they want is your money. They will convince you through fake testimonials too.
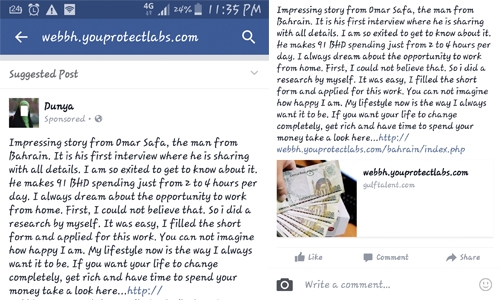
A post by a scammer’s fake profile shares story of a man, supposedly a Bahrain resident, named Omar Safa, who made money using the ‘work at home’
jobs programme.
The post mentions about his interview by the media, and shares quotes from Omar Safa. However, the interview was not published in any publications and the identity of Omar Safa could not be verified.
Experts from Scam Detector, an international fraud prevention organisation, were one of the first to expose the scam.
“Facebook does not have this programme. It’s a fake. Ignore the “Make Millions From The Comfort Of Your Home” deals, especially if they come with a “Limited Positions Available” tag. Do not send any money for any wonder moneymaking kits online. Always do your research and work only for legitimate employers,” warned Scam Detector.
Apparently there is another version of the scam.
“In a different variation of the scam, crooks advertise the term “Facebook Fortunes Home Income Flow”. Displaying a bunch of fake Facebook ‘likes’ and ‘comments’, as well as phony news articles where this programme is featured, criminals lure victims to submit their credit card numbers and charge huge amounts on the spot,” it added.
Most common methods of cyber crime scams
Phishing – when emails are sent pretending to be from a trustworthy source, such as your bank or a client asking for sensitive information including passwords or log-in details. Emails may also contain direct links to websites that are infected with malware.
Spear phishing – a specialised attack targeted on a specific person. Criminals may trawl social media for personal details so they can make their approach more direct and credible.
Physical baiting – a common example is where a criminal leaves a piece of hardware infected with malware, such as a USB stick or CD, where their target is likely to find it. The target then uses it on a personal or work computer, which is then also infected.
Pretexting – when an attacker creates false, usually urgent, circumstances to compel the victim to provide information – for example, they might masquerade as a senior IT manager at your company asking for your login details.
Related Posts